Summary: DRM, Digital Rights Management, the false belief that you can keep pirates from stealing your stuff without punishing your customers. Today's "Doug Goes Off" is about it and few ways that it quickly gets really dumb.
Doug goes off on....DRM (Digital Rights Management)
Monday, 08 March 2010
Doug goes off on....DRM (Digital Rights Management)
Ok, let's say that you are an executive at a software firm. You notice that your last mega-hit
Here's a handy graphic to show how well it works:

Ok, surely parts of that are speculation. Some game designers (and other creators, this would include authors and movie makers and so forth) know that pirates are not the end all and be all of blame sources. Some know that the Zeitgeist simply leaves them behind. Some realize how marketing fails. However, pound for pound, it seems like my chart above is correct. As CD stores around the world bemoan piracy and the loss of "real fans", they rarely seem to note that music marketing is now limited to Top 40 Radio hits (and their reliance on singles), music reviews (and their limits), and word of mouth (with some of the best sources of word of mouth like Youtube being attacked by the companies). Every generation of videogame seems to have worse and worse DRM, eventually leading up to the point where you get ridiculous scenarios like people who paid for a game not being able to play it.
This leads to us getting completely imbalanced pro and cons depending on whether or not we are the consumer or the producer. As consumers, we have lessened gameplay and have to give up some of our security rights to a third party company while spending more (at least relatively) and in exchange we get to buy more product from our favorite companies. As producers, they get free marketing research data through tracking and the illusion of stopping pirates but lose profits due to the cost of DRM. They also suffer the one-way sieve, namely: you lose more fans to DRM than you lose pirates. There are three basic reasons for this:
- There are more pirates than you have more personnel, therefore they have more resources. There will be only a small minority of products where the average per-pirate difficulty in cracking the DRM is greater than the average per-fan difficulty in using the product despite the DRM.
- Some fans will use a hacked version of your product because it works better. This helps to keep the pirating community filled with the very people who want to keep most loyal to your product.
- Pirates don't care about your product, their hobby is cracking it open. The bigger the challenge, the more fun it is. Fans, however, do care about your product and they don't want to feel taken advantage of or put out when using it.
However, see above chart for why this "one way sieve" is not going to be blamed on the right sources. Instead, pirates and fans will get the lion's share of the blame and the cycle will continue.
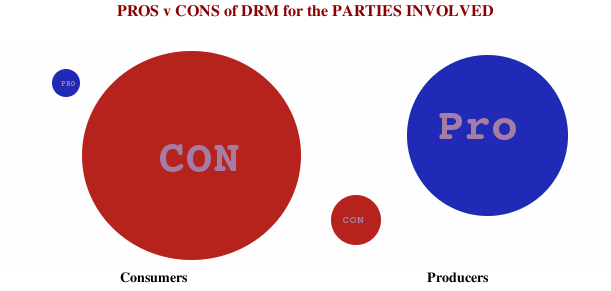
For those curious, there are about as many different DRM schemas as there are products, but here are some of the most basic and widely used:
- Digital Watermarking: Your name and sometimes other personal information (like credit card numbers, addresses, etc) are embedded into the document itself. It makes a shared document more traceable and decreases the likelihood that you will share it with someone else. Not really invasive (not unless you share it) and usually painless on the part of the user, nevertheless could potentially contribute to identity theft.
- Non-specific Passwords: The old-school version of the next one. Older games and other products required a password to open. Can be annoying, since it requires one keeping up with a manual or password book. Not really invasive though, and easily breakable by a simple upload of a text file.
- Physical aspect required: The old disk in the drive system, often breakable by a simple disk-copy method. Could be very annoying depending on how it was carried off.
- Static Encryption: the file is encrypted with a key, usually linked to a user account. Sometimes the key is molded around a password and/or username. Sometimes it is built around a credit-card number. Requires keeping track of that information, but not overall invasive. Can technically share the file if you are willing to share the information.
- Decryption by Application/Device: Some device or application is associated with a user account, usually downloading an encryption key from a server (once), and all files opened by it use that key. Once you set up everything, then it becomes less invasive than in the initial stage.
- Server-side Decryption Key Handling with Decaying Certificate: You have to regularly connect to a server to get approval: once a year, once a month, once a day. Once an hour. Constantly. Really annoying and really invasive.
- Installation of Secondary Application: Supposedly this second will be able to mitigate your primary app's ability to use potentially pirated goods. In order to use a certain product with an application you already have (say: Windows Media Player), you must install this second app that overrides it and confirms you can use your product. Has the potential to hose your primary app and takes up diskspace and RAM. Very annoying and very invasive, especially since every Tom, Dick, and Harry wants to use their own stuff and sometimes it fights amongst themselves.
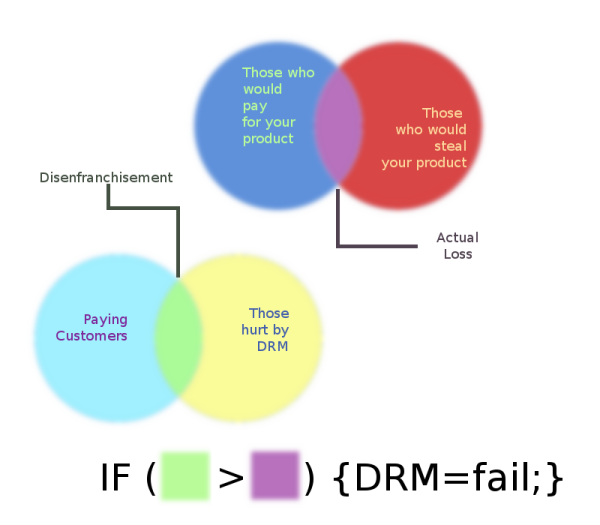
In other words, if the number of people who would have bought your product but stole it is not greater than the number of people who did buy your product but were hurt in their ability to use it, then your DRM schema is only hurting your fans.
The primary focus of this whole entry, as rambling as it is, is to bring up disenfranchisement: those paying customers (like myself) who have paid for a product but are removed from the ability to actually own it or to take full advantage of it. At best DRM guarantees that my satisfaction of a product will have a limit less than an DRMed example of a similar value. At worst, the tenets of DRM may greatly impact my ability to even use my product. This removes and subverts long standing ideals about producer-consumer relations and ends up with the user essentially buying into a contract with the producer that says that the producer will making "adequate" attempts to uphold but does not actually bind the producer to any such thing.
By requiring updates to a program or app to use a product, the producer is able to set how long the shelf-life is (which is as long as it profitable or until they get tired). To repeat, they can cease a product from being used whenever it becomes beneficial for them to do so or at least it becomes non-beneficial for them to upkeep it. How long before some beloved game or book that you enjoy is considered non-profitable by a company? Things don't go...you know...out of print, do they?
They can start limiting things like how often you can access it, what you can do with it, what it means to you. They can track how often you use a product and for how long you use a product. They can be swayed by monetary pressure to not offer an equal product to all systems (the "I'll scratch your back if you scratch mine" model of computer science) or to suddenly drop support of a system. They can force the user to hand over increasing amounts of personal information in order to keep using a service. The consumer must comply with all of the terms handed out in legalese bloated EULAs or get none of the product they have paid for. And none of it has worked yet. The same books and the same movies and the same albums and the same games are out there, on the Internet, for download. All that has happened is fans have been put through cycle after cycle of disenfranchisement.
Sure, there are some of weaker skills who try a few times and give up, but all they have to do is wait and look again and soon someone will have overcome the challenge. There are some products that the DRM might have hosed enough that no one takes a crack at it, but chances are those products weren't all that popular to begin with. If there is a want for it, or just a fun challenge in getting it, then there will probably be a way.
What's more, every successive cycle of DRM creates even more disenfranchised. And, every cycle of disenfranchisement creates more who will not return to the buying side of the pool, next time. They will find someone else's product. They will stop caring about the industry as the whole. Or, they will steal your product next time.
Si Vales, Valeo
file under (...on Life, Law, & Society)
- See other entries for March 10
- See Journal Archives (sorted by year then month)
Where did the comment box go?
Due to most of my friends using alternate means to contact me, and mostly SPAM bots using the comment box method, I have removed it. If you wish to contact me, please feel free to use any human-friendly contact method you wish. Thanks!
dickens of a blog




Written by Doug Bolden
For those wishing to get in touch, you can contact me in a number of ways

This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License.
The longer, fuller version of this text can be found on my FAQ: "Can I Use Something I Found on the Site?".
"The hidden is greater than the seen."



Comment(s)
If you wish to comment, please use the form below or contact me in some other way and I'll add it as soon as possible. Thanks!